Privileged Account Management
It is
a centralized solution that secures privileged access and monitors privileged
sessions. It provides unalterable audit trails and behavioral analysis reports
on privileged user activity. These resources can be useful when making security
decisions and can help prevent the spread of malicious software to other
systems.
The core of the WALLIX Bastion allows you to secure your privileged accounts
and support your teams regulatory compliance efforts.
Session Manager: Monitors all activity and controls
privileged access in real-time to prevent and to detect malicious activity.
Password Manager: Manages passwords and SSH keys in a consolidated vault, and enables super-administrators to regain control over access governance by managing password complexity and guaranteeing that passwords are not divulged or hijacked.

Access Manager: His module provides security teams with a centralized console for privileged access management. It provides an exhaustive real-time list of all privileged users logins, sessions, and actions to mitigate risk and prevent cyber-attacks
Endpoint Security
Endpoint security is an approach to the protection of end-user devices from being exploited by malicious actors and campaigns.
Endpoint security systems protect these endpoints on a network or in the cloud from cyber security threats. It delivers layered next-gen security that consistently ranks first in independent tests. It leverages a single management platform to reduce the cost of building a trusted environment for all endpoints. Enterprise Security lets organizations enable dedicated protection for Datacenters, Physical Endpoints, Mobile Devices, and Exchange mailboxes with the flexibility to choose which security services to deploy. All services are seamlessly managed from the highly scalable and robust on-premise GravityZone Control Center console.

Endpoint Security Solution Benefits
World's Strongest Prevention
Automatically stop 99% of attacks with #1 ranked prevention that combines over 30 technologies, such as tunable machine
learning, sandbox analyzer, anti-exploit and behavioral analysis
Attack Forensics and Visualization
Gain insight into your threat environment and perform forensic analysis by zeroing in on attacks specifically aimed at your
organization. Visualize the attack kill chain and perform required remediation
Endpoint Hardening and Risk Management
Strengthen security posture with integrated device- and application control, patching, encryption and other technologies. Leverage integrated Risk Management and Analytics to continuously assess, prioritize, and address misconfigurations and vulnerabilities. Including the human triggered ones

Unified Endpoint
Management
Unified endpoint management allows IT to manage all types of endpoints—iOS, Android, Windows, Chrome, Mac and more—through a single console. With the right mix of mobile application management (MAM) and enterprise mobility management (EMM) features, companies can confidently let employees work on any endpoint, from any location. All while protecting company data and keeping users’ personal information untouched.
With one unified view of all endpoints, IT can provide seamless access to the apps and data employees need to be productive. Onboarding new devices can be done in a matter of minutes, and users can self-enroll quickly and easily.

What can you do with Endpoint Management
Manage every endpoint from the same console and get a single view of multi-device users Secure every endpoint
Empower employees to work from anywhere with a secure digital workspace experience
Let employees use personal devices while keeping sensitive data protected
Single Sign-On
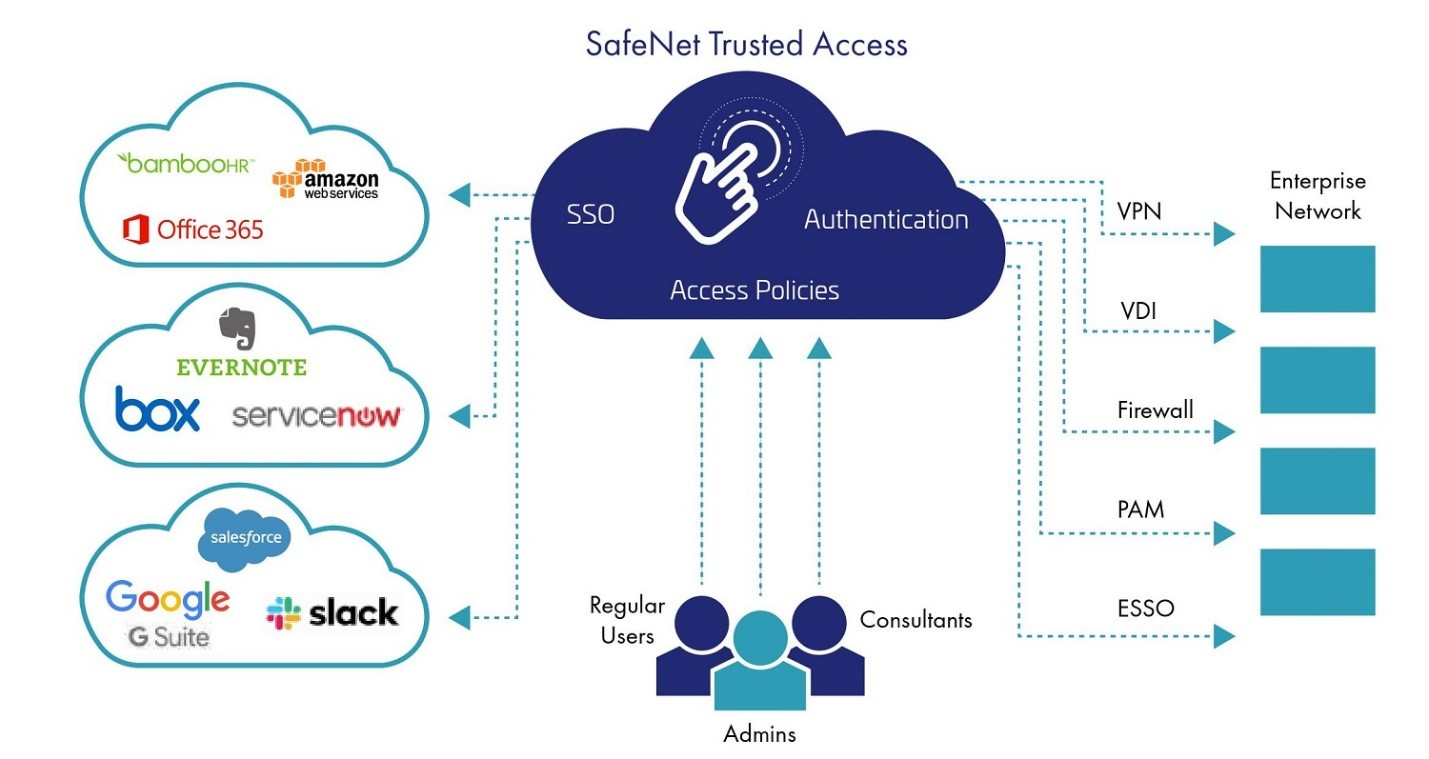
By combining the convenience of single sign-on with granular access policies, organizations can tighten access controls, and reduce password fatigue–the cumulative exhaustion experienced by many due to the ongoing need to create, remember, update and reset an excessive number of passwords on a daily basis. By validating identities, enforcing access policies and applying Smart Single Sign-On, organizations can ensure secure, convenient access to numerous cloud applications, and reduce management overhead by centrally defining and enforcing access controls from one easy-to-navigate console.
Single Sign-On Benefits
Identity-as-a-service efficiencies
Core Capabilities
Smart Single Sign-On lets users log in to all their cloud applications with a single identity, eliminating password fatigue, frustration, password resets and downtime.
In this way, users may authenticate just once in order to access all their cloud applications, or provide additional authentication as configured in the policy.
Fine-grained access policies let you define which users can access which apps, using which authentication methods, as well as define conditions under which user access should be denied. Policies can be defined to balance between security and usability considerations, and can be customized per compliance mandate, user group, or cluster of applications.
Context-based authentication enhances user convenience by assessing contextual parameters to determine whether a login attempt is secure. When a login attempt is considered secure, the user is granted immediate access. When it is not considered secure, a broad range of additional authentication methods are available.