DNS Protection
With our Advanced DNS protection solution, your business is always up and running, even under a DNS-based attack. It blocks the widest range of attacks, such as volumetric attacks, NXDOMAIN, exploits and DNS hijacking. Unlike approaches that rely on infrastructure overprovisioning or simple response-rate
limiting, Advanced DNS Protection intelligently detects and mitigates DNS attacks while responding only to legitimate queries by using constantly updated threat intelligence, without the need to deploy security patches. With our solution, you can take network reliability to the next level by ensuring that your critical infrastructure—and your business—keep working at all times
Key Features
Monitors, detects and stops all types of DNS attacks— including volumetric attacks non-volumetric attacks, such as DNS exploits and DNS hijacking—while responding to legitimate queries. It also maintains DNS integrity, which DNS hijacking attacks can compromise. It provides a solid foundation for security, enabling five nines availability for your network.
It uses Threat technology to automatically update protection against new and evolving threats
as they emerge. Threat Adapt applies independent analysis and research to evolving attack techniques, including what threat specialists have seen in customer networks, to update protection. It automatically adapts protection to reflect DNS configuration changes.
Your organization can easily view prior or current DNS attacks and improve operational efficiency through our rapid threat remediation. The Advanced DNS Protection also provides a single view of attack points across the network and attack
sources, supplying the intelligence necessary for threat management
Online Fraud Detection
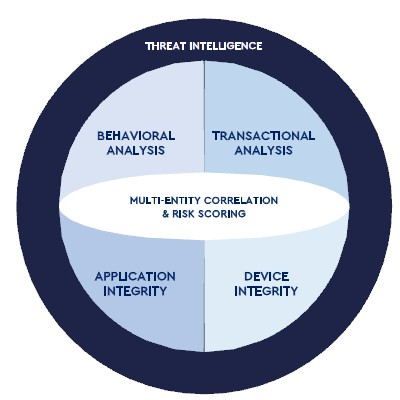
Our solution helps embrace DX initiatives without compromising security, by continuously monitoring and identifying in real-time any sign of malware infection or complex threat scenarios representing targeted attacks to your extended perimeter.
1) Detect integrity of applications & data against advanced attack techniques (e.g. MITB, MITM) used for data tampering and credential hijacking
2)Analyze anomalous behavior, such as users using new devices or accessing data from unusual locations at unusual time (e.g. outside business hours)
3) Analyze suspicious activities involving sensitive data (e.g. credit card numbers) representing potential slow & low data exfiltration scenarios
4) Create rules to correlate multiple Indicators of Compromise (IOCs) and automatically send alerts and execute response actions
5) Adopt threat protection mechanisms that enable user sessions to be safe even in presence of infected endpoints and MITB or MITM attacks
Our solution delivers client-less and application-transparent threat detection and protection for your on-line services
- Patented Full Content Integrity (FCI) continuously verifies full application integrity (DOM/XHR/API)
- Deep threat visibility automatic extraction of threat evidence (e.g. malicious web-injects and mobile apps)
- Patented Dynamic Application Encryption (DAE) to enable safe transactions from infected endpoints
- Client-less – no agent deployed and passive mobile SDK – no touch of application backend infrastructure
- User-transparent – no impact on end-user experience, content delivery and endpoint performance
- Application-independent – no changes required to application code – no re-training upon new releases
- Open architecture and comprehensive REST APIs – integrates any Transaction Monitor, Case Mgmt, SIEM
- Scalable to continuously monitor full application perimeter and analyze millions of events / day
- Deployed either on-premise or over the Cloud
Security Control Validation
Provides you with the evidence to manage and report on your organization’s systemic cyber security risk.
We arm you with the ability to optimize your spend on your security stack by testing your configurations with real attacks, not simulations, in the production environment to pinpoint which systems or tools are leaving assets at risk. We proactively identify configuration issues and expose the gaps across your people, process, and technology
Security Validation instruments IT environments at scale to test the effectiveness of network, endpoint, email and cloud controls. Continuously execute tests and analyze results to proactively alert on drift from a known-good baseline and validate control configuration
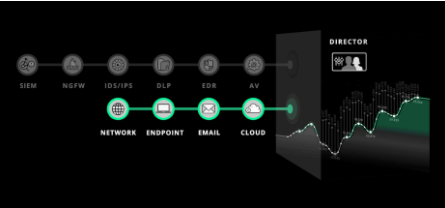
Generate proof that your controls are protecting critical assets
By providing quantifiable data and the ability to translate technology information to business language, you can demonstrate accountability and proactive reporting on the status of your defenses to executive leadership
Identify the most relevant and impactful threats targeting your organization so that you can automatically test defenses with the same attack behaviors your potential adversaries use to breach other companies
Test your configurations with real cyber security attacks, not breach and attack simulations, in the production environment so that you can pinpoint which systems or security tools are leaving assets at risk.
Provide empiric reports that reveal exactly how people, process and technology respond to a specific cyber threat ahead of time. Effectively display what the past incident report will look like before the actual incident occurs so that you can make educated investment decisions to improve cyber security risk management.
Vulnerability Assessment
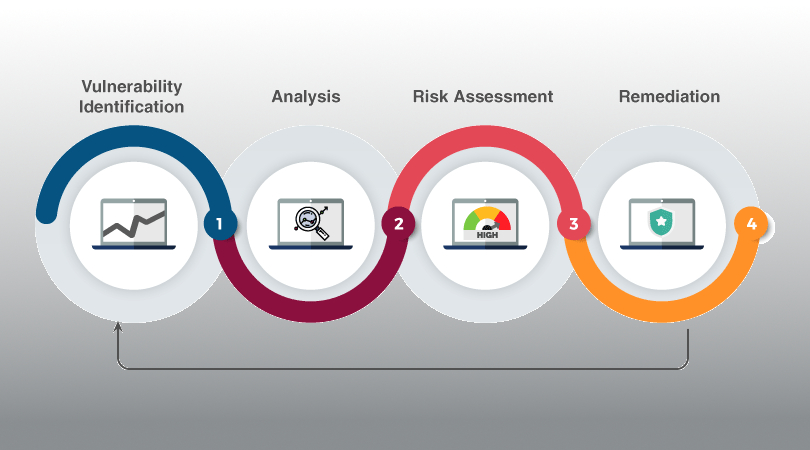
The industry’s most widely deployed vulnerability scanner helps you reduce your organization’s attack surface and ensure compliance in physical, virtual, mobile and cloud environments. It features high-speed asset discovery, configuration auditing, target profiling, malware detection, sensitive data discovery and vulnerability analysis.
Automates point-in-time assessments to help quickly identify and fix vulnerabilities, including software
flaws, missing patches, malware, and misconfigurations, across a variety of operating systems, devices and applications.
Vulnerability Assessment Solution Benefits
60K CVEs – the most in the industry. Nessus scans more technologies and uncovers more vulnerabilities than competing solutions
Identifies the vulnerabilities that need attention with high-speed, accurate scanning and minimal false-positives.
Policy creation is simple and only requires a few clicks to scan an entire corporate network
Vulnerability Assessment & Penetration Testing
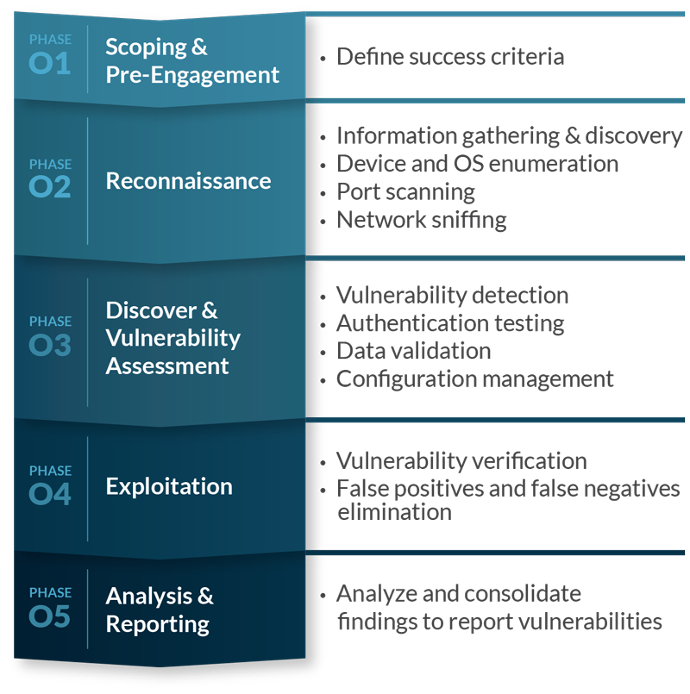
Penetration testing is a proactive approach to discovering exploitable vulnerabilities in your computer systems and network as well as the devices within the network.
Vulnerability Assessment gives clients the opportunity to uncover potential issues in their information systems, and offer recommendations to eliminate or reduce the level of risk.
Our aim is to reveal any hidden threats and vulnerabilities so you can be a step ahead of the attacks, and also gives you the opportunity to address them.
Penetration Testing Methodology
Our Security Assessment Services
Our penetration testing services are customized from ‘Black, White or Grey Box’ perspectives, depending on clients needs: