Patch Management
Keeping up with the constant stream of security threats and patches is an ongoing drain on IT staff.
Organizations must be able to research, evaluate, test, and apply patches across the enterprise easily and automatically. And with the majority of vulnerabilities affecting third-party applications, patching and updating operating systems just isn’t enough. With our patch management solution, your enterprise
can discover, assess, and remediate thousands of client systems comprehensively, consistently, and
regularly, based on policies you define and without saturating your network or disrupting user
productivity.
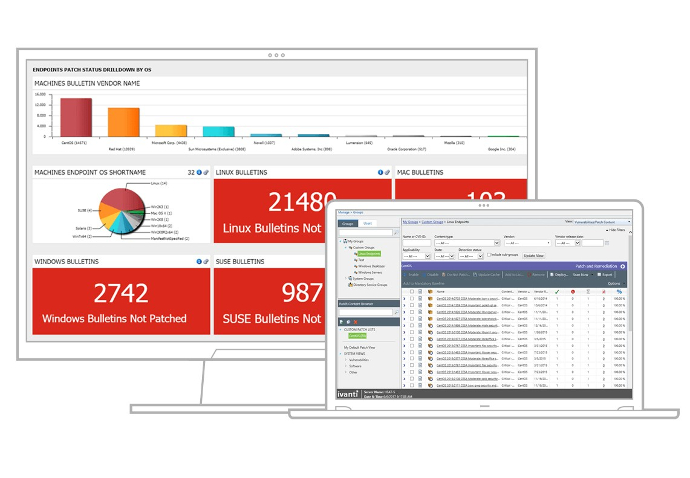
Patch Management Benefits
Establish and automate consistent policies for patching all of your assets, even those that are mobile, remote, or asleep.
Detect and remediate OS and third-party app vulnerabilities on various systems, to comply with laws and regulations.
Eliminate issues that slow user devices, and patch at the right time, under the right conditions, to minimize the impact on users.
Hardware Security Module
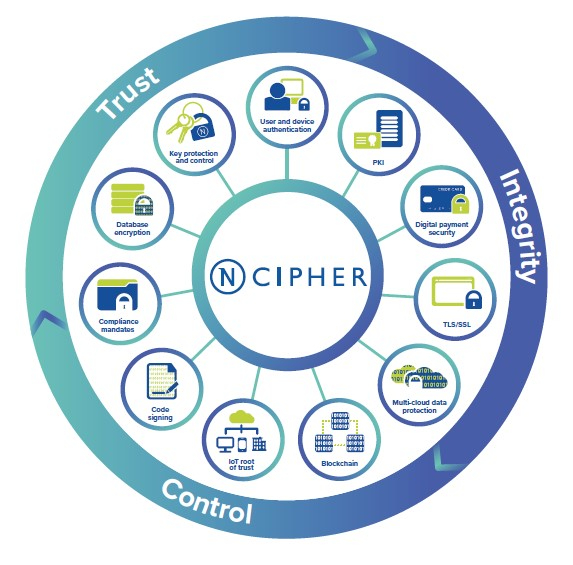
Our cryptographic solutions secure emerging technologies – IoT, blockchain, digital payments – and help meet new compliance mandates, with the same proven technology that global organizations depend on today to protect against threats to their sensitive data, network communications and enterprise infrastructure.
The HSM can do the following:
1) Generate strong encryption and signing keys
2) Provide a protected environment to Sign and verify data and certificates & Encrypt and decrypt data
3) Protect keys in storage
Family of HSM's
A network-attached appliance for high-performance data center environments.
- Network attached appliance
- Shared crypto resource
- High performance
- High availability
A PCIe server-embedded card for high-volume applications
- Server-embedded card
- Dedicated processing
- High performance
- Compact PCIe design
A USB-connected model for portable, low-volume and developer applications
- Portable HSM
- Use with PC/laptop
- Small footprint
- USB interface
Email Security
More than 90% of targeted attacks start with email, and these security threats are always evolving. Proofpoint Email Protection provides multiple layers of security to stop malware and non-malware threats, such as email fraud. It can control all aspects of inbound and outbound email to detect and block threats, and prevent confidential information from getting into the wrong hands.
Email Security solution is deployed as a cloud service or on premises.
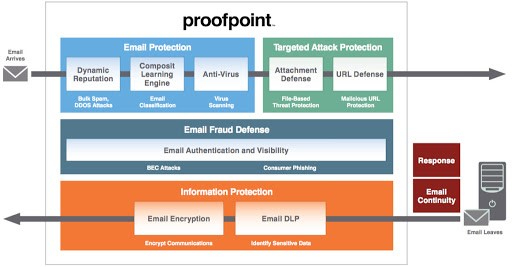
Email Security Benefits
Email Protection allows you to set up robust email filtering policies as a first step in routing email to users. You can create detailed firewall rules based on your needs. Even set up policies for anti-virus. We also leverage user bulk mail actions to improve the accuracy of future detection and classification.
Dynamically block non-malware threats (such as BEC) trying to trick your people into sending money and sensitive corporate data.
Dynamically classify and quarantine email using seven unique categories.
Maintain email communications if your on-premises or cloud-based email server fails.
Data Loss Prevention
Understanding the internal and external threats, along with the resource challenges to manage the growing collection of products, Digital Guardian is the first and only solution that unifies internal and external data protection solutions into a single console.
The Digital Guardian data protection platform consolidates data loss prevention, endpoint detection & response and user & entity behavior analytics to deliver the only enterprise threat aware data protection solution – all from a single analytics and reporting console, tailored for information security professionals.

Our platform, performs on traditional endpoints, across the corporate network, and cloud applications, making it easier to see and block threats to sensitive information
DLP Solution Relies on 3 Essential Elements to Inform and Effect Data Security
- System Events
- User Events
- Data Events
- Filters out the noise
- Accelerates investigation
- Delivers incident discovery
- Don’t slow down your business
- Across network, storage, cloud, and endpoints
- Enforceable on all OSs (Windows, Linux, Mac)